Exploit Routers on an Unrooted Android Phone.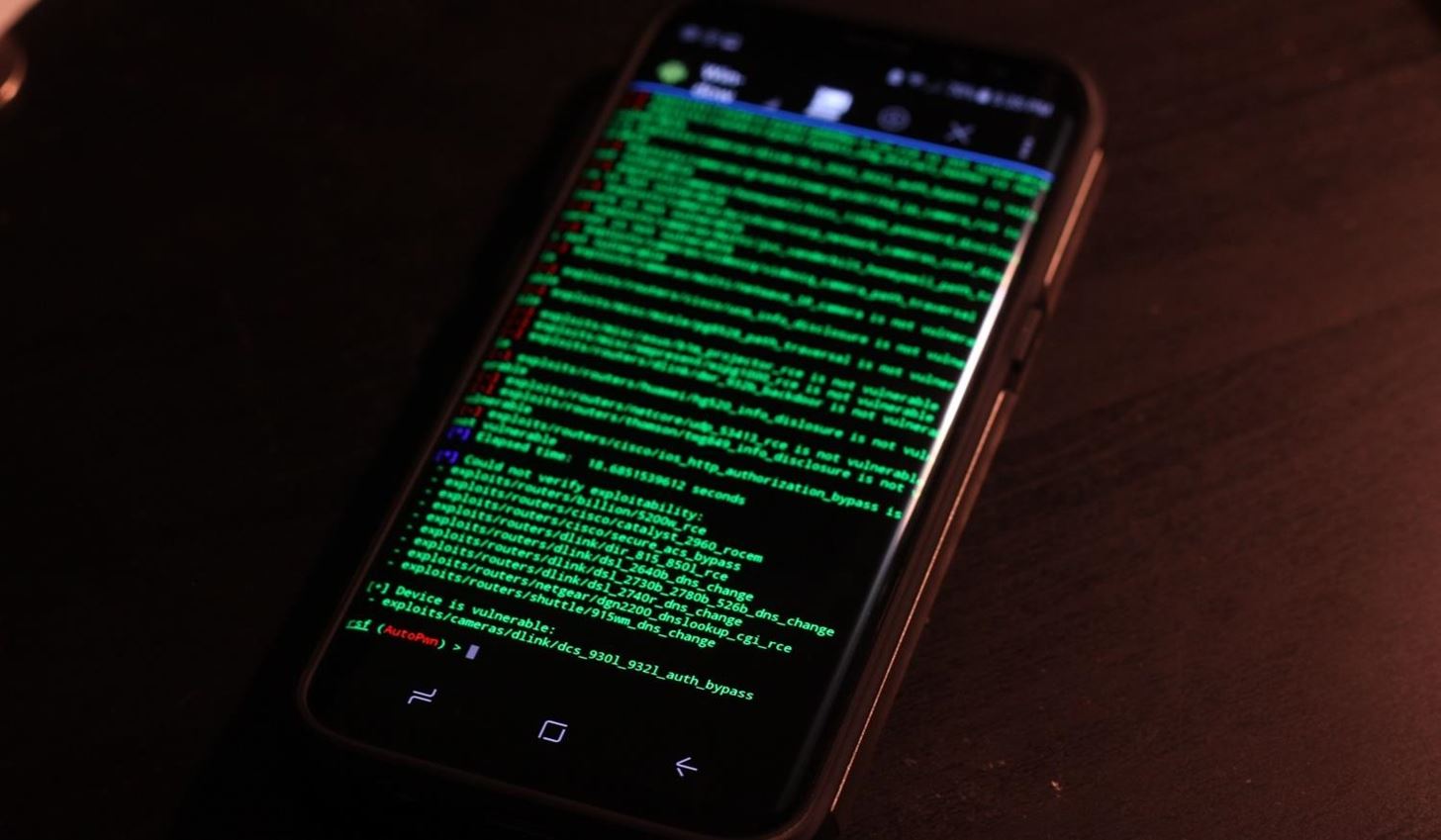
I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tutorial will walk you through setting up RouterSploit to work on an unrooted Android phone. This allows you to pwn any vulnerable router you can connect your smartphone to. Doing so takes seconds and shows the power of running Debian Linux tools on the device you carry everywhere.
RouterSploit vs Routers
Routers are our gateway to the world. They route our internet traffic, encrypt our traffic to protect our privacy, and link us to other devices on our local networks and on the World Wide Web.
Most people take this wonderful device for granted, assuming once one is plugged in and providing the internet, the job of setting it up is done. Not knowing the router is actually its own Linux computer, most people simply leave the default password on the router's administrator panel or never bother logging in to install any security updates.
If this sounds like you, you should probably go change the password on your router before reading the rest of this tutorial.
Don't Miss: How the CIA & Hackers Exploit Your Router with RouterSploit
Because routers are neglected, they frequently have commonly known vulnerabilities that can be exploited with the right program. RouterSploit takes advantage of the most common vulnerabilities and default settings, allowing you to quickly assess and exploit a router from any device the supports the Python script.
Debian Linux on Android
In order to run hacking tools on an Android phone, most tools require root access, which is not always easily done or safe. In order to run RouterSploit on the best available phone, an app called GNURootDebian takes the work out of setting up a Debian system, which is what Kali is, on an Android phone.
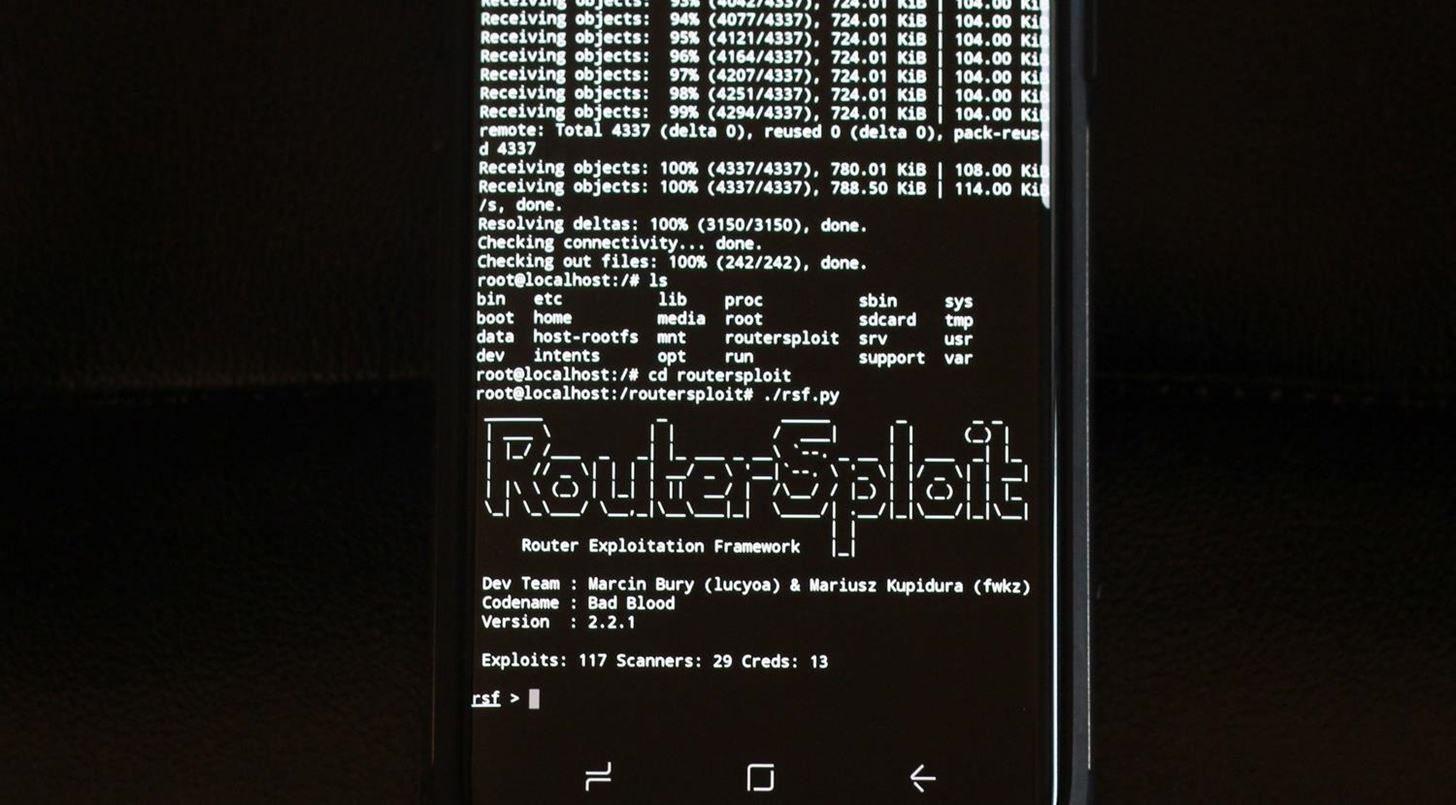 We've got RouterSploit running on an unrooted Android!
We've got RouterSploit running on an unrooted Android!
Kali helpfully ensures that the majority of our dependencies are installed, so we'll need to install a lot more dependencies on our Android version of Debian to make sure we have everything we need. This method doesn't require root or any weird permissions and can be used to run Linux Python tools from an Android phone. While packet injection isn't supported, frameworks like RouterSploit work and are very effective.
Using an Attack Framework on Android
The Android environment allows for a neat stack of wireless attack technologies to guide your tactics. Within one device, various apps will help you detect, connect to, and defeat any open AP. My "stack" of Android apps to defeat routers is as follows.
For detection and identification of wireless networks in an area, Wigle Wifi Wardriving allows you to see, log, and interact with any and all wireless networks transmitting in your area
For scanning of networks and identification of likely targets by manufacturer, IP address, and services available, Fing Network Scanner will scan the entirety of any network you are connected to and return detailed information about each connected device.
Once a device has been targeted on the network to attack, RouterSploit's Autopwn scanner will throw every available exploit at the target and see which stick, often taking less than a minute on a Samsung Galaxy phone.
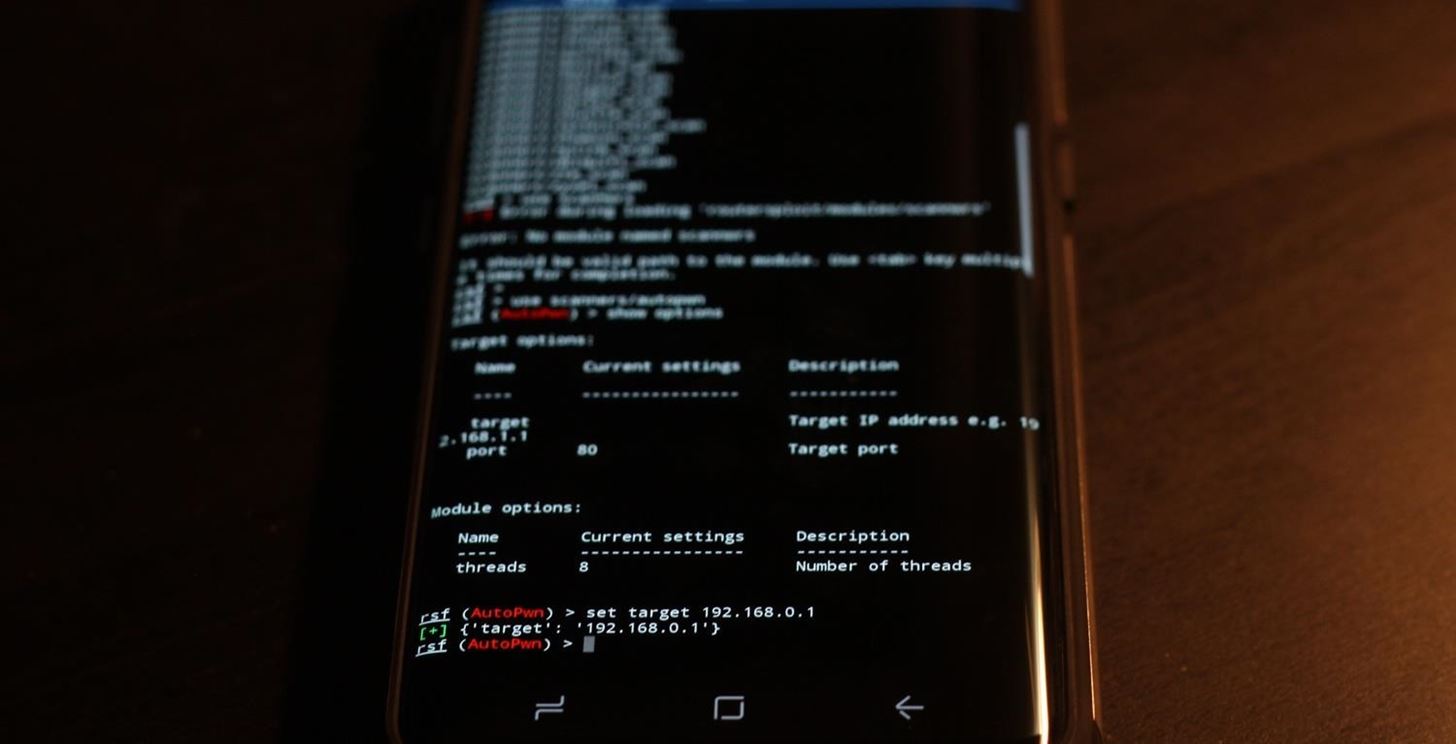
Unrooted Android Burner Phones as Attack Platforms
Using powerful Linux frameworks on Android gives us another way to use something common to hack in plain sight. Even if someone knows what you're doing on your phone isn't normal, it's still a lot less suspicious than pulling out custom hardware to preform a task a generic burner Android phone can accomplish.
For More on Attack Frameworks, Check Out: Null Byte's Series on Metasploit Basics
It is often said that the best weapon to use during a moment of opportunity is the one you know you'll have with you, and hacking tools are no exception. With the ability to quickly set up an Android phone for offensive use, GNURoot Debian allows anyone to begin auditing router security without any specialized tools. Soon, you will learn to seize control of these precious, internet-giving devices while appearing like you're still looking for Pokémon.
What You Need to Get Started
The beauty of this setup is that you just need an Android phone. I'm using a Samsung Galaxy S8 because carrying around a giant piece of curved screen glass reminds me of how fragile life is, but you can use any Android phone that supports GNURoot Debian.
Step 1Installing GNURoot Debian
To begin, we'll install GNURoot Debian, which will give us the ability to run Debian Linux on an unrooted Android device. In the Google Play Store, search for GNURoot Debian or follow this link.
 You can tell he's a good time because of the goatee.
You can tell he's a good time because of the goatee.
Download the app (at 60 MB, it may take a bit on a slow connection). Once the app is installed, it's time for your first run. On starting for the first time, you'll see the Debian environment being set up as a bunch of text scrolling very quickly across the screen.
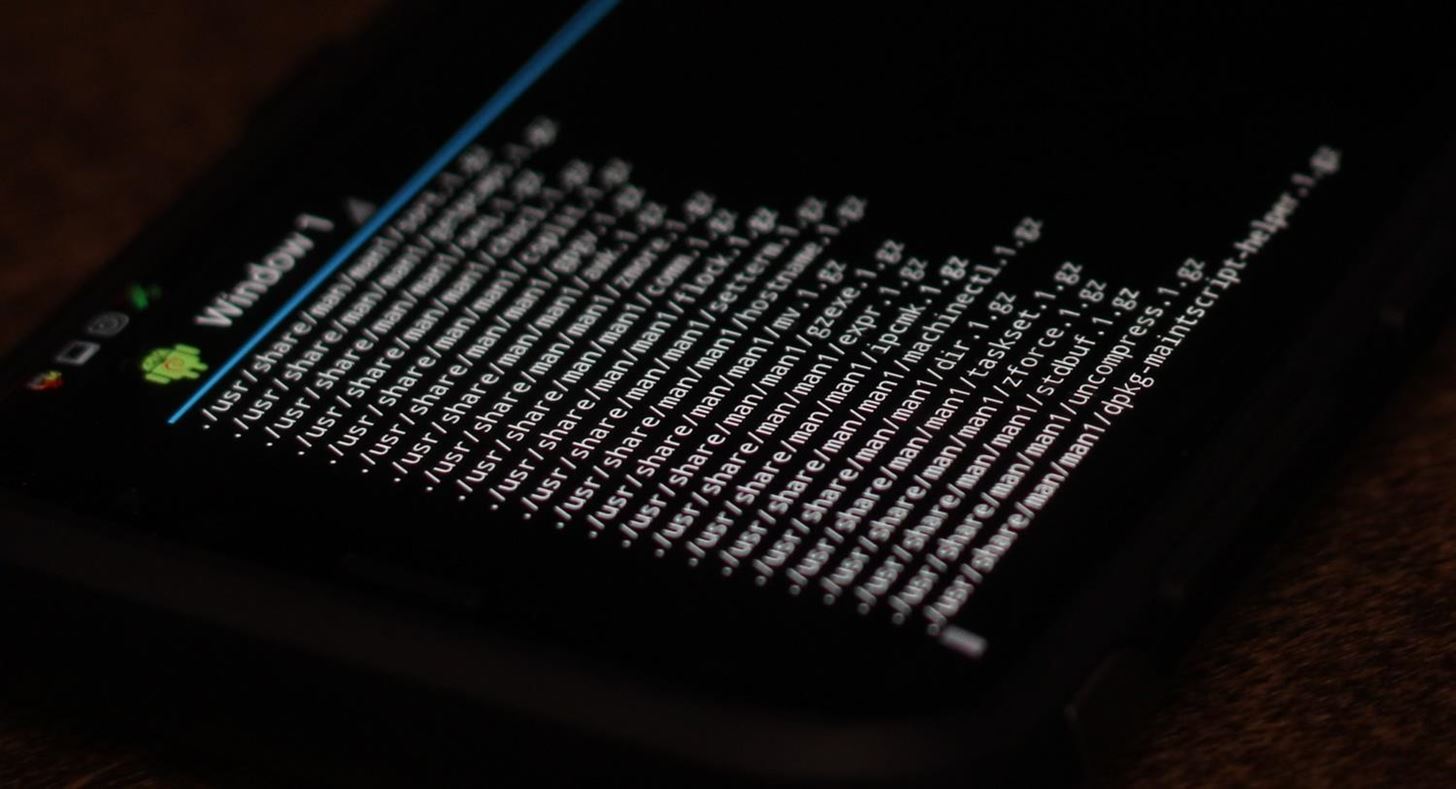
More dependencies loading.Image by SADMIN/Null Byte
Let the setup complete for a few minutes, and you should see the following screen when installation is complete.
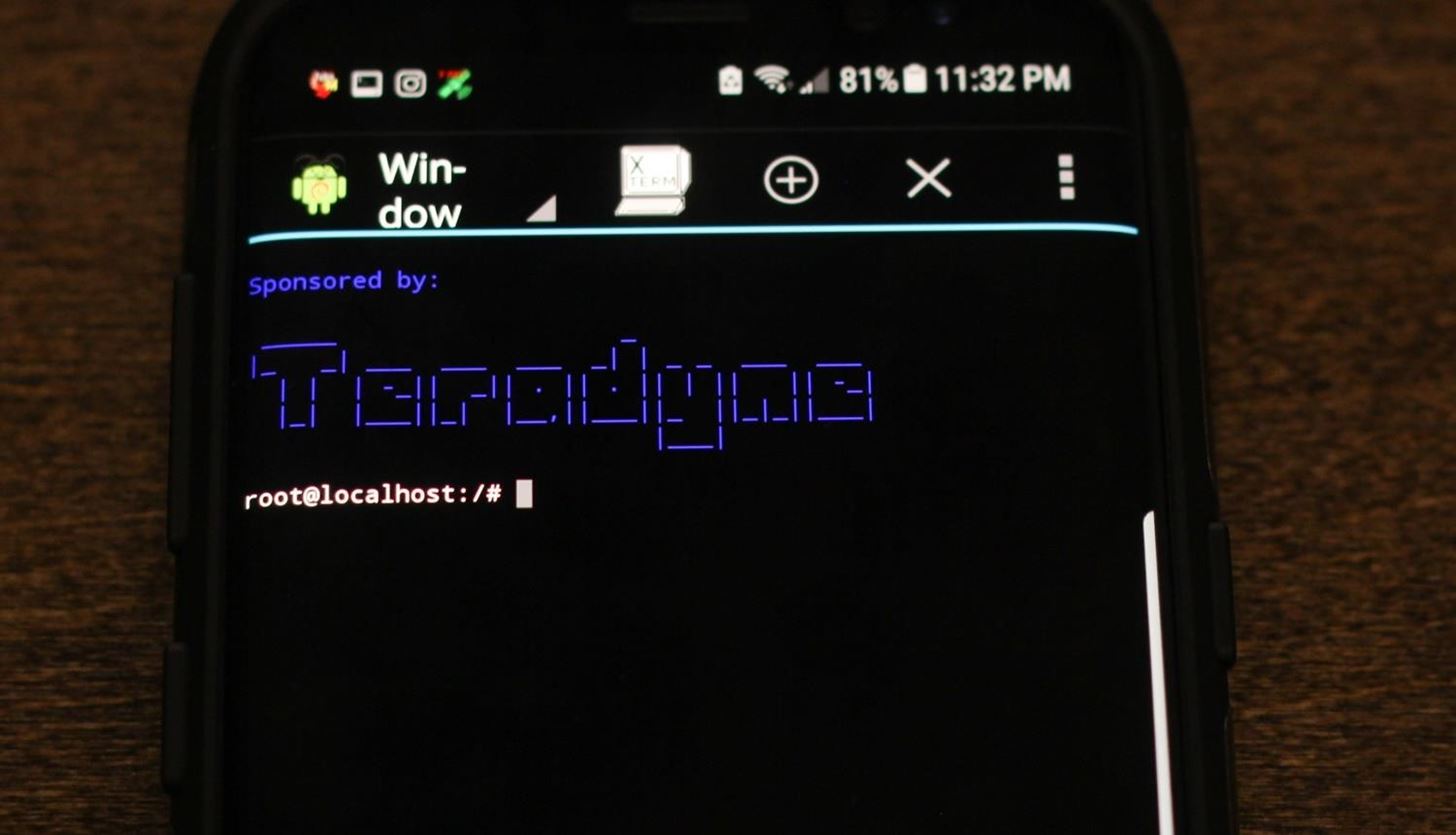 Debian Linux is running on Android.Image by SADMIN/Null Byte
Debian Linux is running on Android.Image by SADMIN/Null Byte
Once Debian Linux is installed, it's time to start installing dependencies.
Step 2Installing Dependencies
Debian Linux on Android doesn't come with any special dependencies preinstalled like Kali, so we'll have to start from scratch on a lot of things. In particular, we'll need Python to run our desired module. First, let's update our version of Debian with the following.
apt-get update
Next, let's install some of the tools we'll need to fetch and install RouterSploit:
apt-get install sudo
sudo apt-get install git-core
This will install git and sudo, so you can fetch RouterSploit from GitHub and execute commands as sudo.
sudo apt-get install python-dev python-pip libncurses5-dev git
Step 3Installing RouterSploit
Once the dependencies are all installed, it's time to grab RouterSploit by typing the following.
git clone https://github.com/reverse-shell/routersploit

Look at all these beautiful dependencies.Image by SADMIN/Null Byte
Step 4Running RouterSploit for the First Time
Upon installing RouterSploit, you'll want to run it for the first time to check that it's working. Navigate to the home folder by typing the following.
cd routersploit
Then run the Python script with this:
sudo python ./rsf.py
After a few seconds to load, you should see the RouterSploit splash screen. From here, the interface is similar to Metasploit, with the primary commands being:
use (module)
set (variable)
show options (shows module options)
check (checks to see if target is vulnerable to exploit)
run (runs the exploit module against the target)
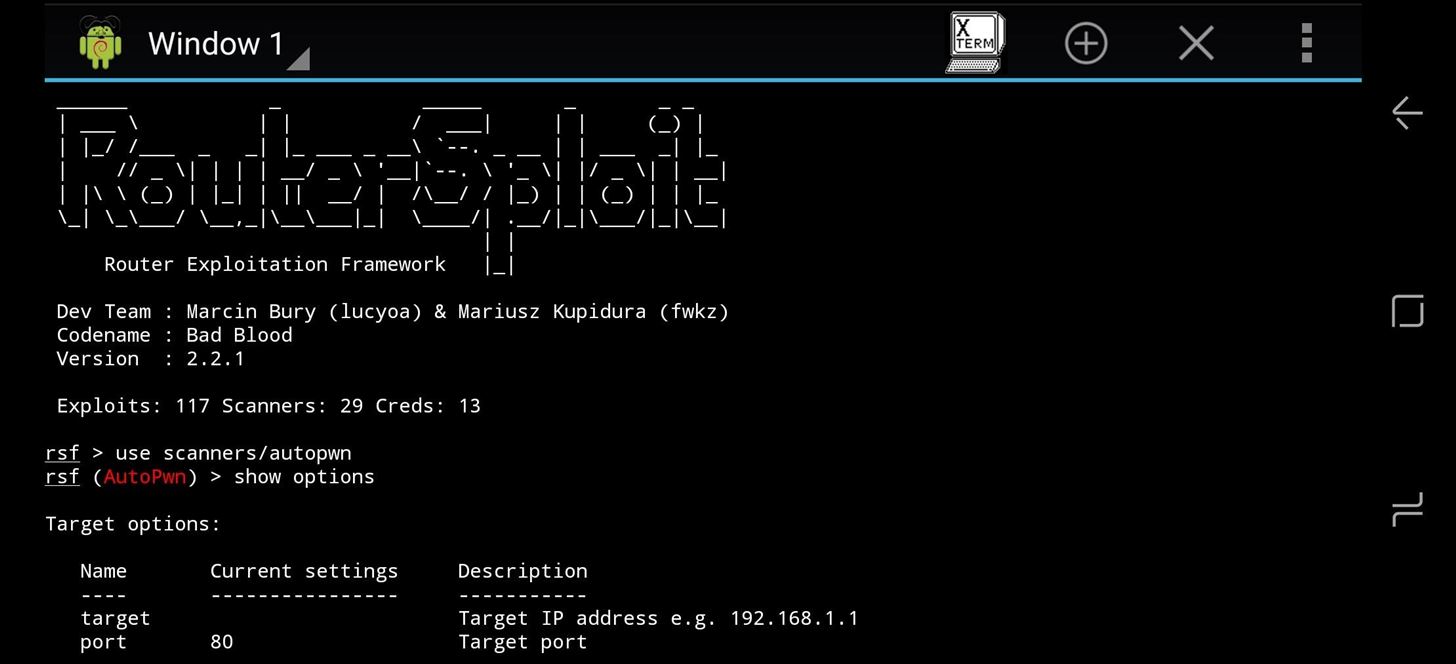
The module we'll be running is Autopwn, which we can select by typing the following.
use scanners/autopwn
This will open the Autopwn scanner to begin scanning a target.
Step 5Setting & Prosecuting a Target
With the Wigle Wifi Wardriving app installed on your Android phone, it's easy to see nearby wireless networks. As soon as you gain access to a Wi-Fi network, either an open network or by gaining the password, you'll be able to scan the network to find all devices on it with Fing or another network scanner.
Once you locate the IP address of your target, it's time to put it into Autopwn. To see the available options on any module, type the following.
show options
In this case, we'll be setting the target IP to that of the router we want to attack. To do so, enter this into the terminal:
set target IP_address_here
 Here, we set the target for the Autopwn scan with the IP address of the target.
Here, we set the target for the Autopwn scan with the IP address of the target.
Replace IP_address_here with the IP address of the router, and hit enter. This should set the target to the router. To double check, type show options again. When you're satisfied with the result, type run and hit enter to begin the module. The module will run, presenting a list of found vulnerabilities at the end of the scan.
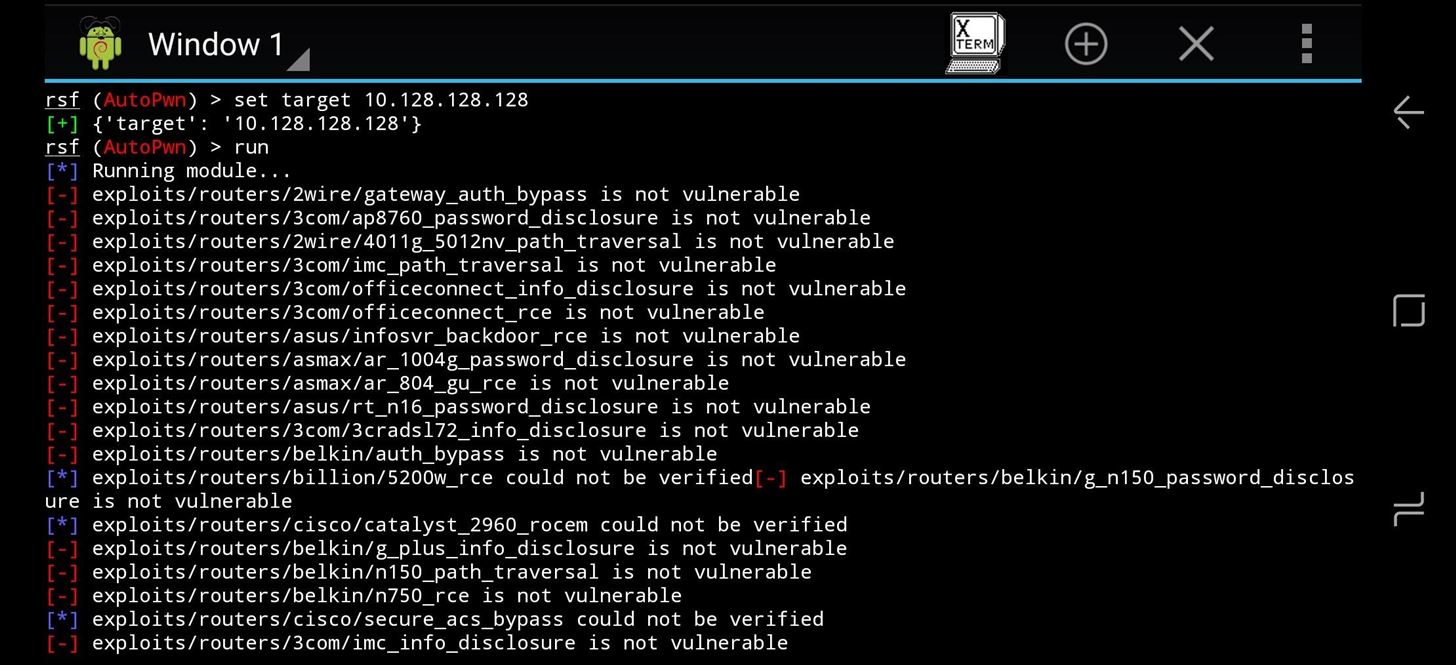
Here, we see a scanning run starting against a target.
Step 6Exploiting Found Vulnerabilities
When Autopwn finds a vulnerability, exploiting it couldn't be easier. After the scan is complete, type use and then copy and paste the path provided by Autopwn to the exploit. For example, running the exploits/cameras/dlink/dcs_9301_9321_auth_bypasswould be done by typing:
use exploits/cameras/dlink/dcs_9301_9321_auth_bypass
As before, we can set the target with:
set target IP_address_here
Once the target is set to our desired IP address, you can run check to verify the device is vulnerable. When you're ready to exploit, type run and the exploit module will run.

This device is vulnerable!
Warning
Even if the router is left completely undefended and is easy to pwn, that doesn't make it legal. Make sure you have permission to audit the router you're pwning, as the Autopwn scanner makes a lot of noise and may be detected by active security measures.

BY.MICKY VERMA
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.
I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tutorial will walk you through setting up RouterSploit to work on an unrooted Android phone. This allows you to pwn any vulnerable router you can connect your smartphone to. Doing so takes seconds and shows the power of running Debian Linux tools on the device you carry everywhere.
RouterSploit vs Routers
Routers are our gateway to the world. They route our internet traffic, encrypt our traffic to protect our privacy, and link us to other devices on our local networks and on the World Wide Web.
Most people take this wonderful device for granted, assuming once one is plugged in and providing the internet, the job of setting it up is done. Not knowing the router is actually its own Linux computer, most people simply leave the default password on the router's administrator panel or never bother logging in to install any security updates.
If this sounds like you, you should probably go change the password on your router before reading the rest of this tutorial.
Don't Miss: How the CIA & Hackers Exploit Your Router with RouterSploit
Because routers are neglected, they frequently have commonly known vulnerabilities that can be exploited with the right program. RouterSploit takes advantage of the most common vulnerabilities and default settings, allowing you to quickly assess and exploit a router from any device the supports the Python script.
Debian Linux on Android
In order to run hacking tools on an Android phone, most tools require root access, which is not always easily done or safe. In order to run RouterSploit on the best available phone, an app called GNURootDebian takes the work out of setting up a Debian system, which is what Kali is, on an Android phone.
 We've got RouterSploit running on an unrooted Android!
We've got RouterSploit running on an unrooted Android!Kali helpfully ensures that the majority of our dependencies are installed, so we'll need to install a lot more dependencies on our Android version of Debian to make sure we have everything we need. This method doesn't require root or any weird permissions and can be used to run Linux Python tools from an Android phone. While packet injection isn't supported, frameworks like RouterSploit work and are very effective.
Using an Attack Framework on Android
The Android environment allows for a neat stack of wireless attack technologies to guide your tactics. Within one device, various apps will help you detect, connect to, and defeat any open AP. My "stack" of Android apps to defeat routers is as follows.
For detection and identification of wireless networks in an area, Wigle Wifi Wardriving allows you to see, log, and interact with any and all wireless networks transmitting in your area
For scanning of networks and identification of likely targets by manufacturer, IP address, and services available, Fing Network Scanner will scan the entirety of any network you are connected to and return detailed information about each connected device.
Once a device has been targeted on the network to attack, RouterSploit's Autopwn scanner will throw every available exploit at the target and see which stick, often taking less than a minute on a Samsung Galaxy phone.

Unrooted Android Burner Phones as Attack Platforms
Using powerful Linux frameworks on Android gives us another way to use something common to hack in plain sight. Even if someone knows what you're doing on your phone isn't normal, it's still a lot less suspicious than pulling out custom hardware to preform a task a generic burner Android phone can accomplish.
For More on Attack Frameworks, Check Out: Null Byte's Series on Metasploit Basics
It is often said that the best weapon to use during a moment of opportunity is the one you know you'll have with you, and hacking tools are no exception. With the ability to quickly set up an Android phone for offensive use, GNURoot Debian allows anyone to begin auditing router security without any specialized tools. Soon, you will learn to seize control of these precious, internet-giving devices while appearing like you're still looking for Pokémon.
What You Need to Get Started
The beauty of this setup is that you just need an Android phone. I'm using a Samsung Galaxy S8 because carrying around a giant piece of curved screen glass reminds me of how fragile life is, but you can use any Android phone that supports GNURoot Debian.
Step 1Installing GNURoot Debian
To begin, we'll install GNURoot Debian, which will give us the ability to run Debian Linux on an unrooted Android device. In the Google Play Store, search for GNURoot Debian or follow this link.
 You can tell he's a good time because of the goatee.
You can tell he's a good time because of the goatee.Download the app (at 60 MB, it may take a bit on a slow connection). Once the app is installed, it's time for your first run. On starting for the first time, you'll see the Debian environment being set up as a bunch of text scrolling very quickly across the screen.

More dependencies loading.Image by SADMIN/Null Byte
Let the setup complete for a few minutes, and you should see the following screen when installation is complete.
 Debian Linux is running on Android.Image by SADMIN/Null Byte
Debian Linux is running on Android.Image by SADMIN/Null ByteOnce Debian Linux is installed, it's time to start installing dependencies.
Step 2Installing Dependencies
Debian Linux on Android doesn't come with any special dependencies preinstalled like Kali, so we'll have to start from scratch on a lot of things. In particular, we'll need Python to run our desired module. First, let's update our version of Debian with the following.
apt-get update
Next, let's install some of the tools we'll need to fetch and install RouterSploit:
apt-get install sudo
sudo apt-get install git-core
This will install git and sudo, so you can fetch RouterSploit from GitHub and execute commands as sudo.
sudo apt-get install python-dev python-pip libncurses5-dev git
Step 3Installing RouterSploit
Once the dependencies are all installed, it's time to grab RouterSploit by typing the following.
git clone https://github.com/reverse-shell/routersploit

Look at all these beautiful dependencies.Image by SADMIN/Null Byte
Step 4Running RouterSploit for the First Time
Upon installing RouterSploit, you'll want to run it for the first time to check that it's working. Navigate to the home folder by typing the following.
cd routersploit
Then run the Python script with this:
sudo python ./rsf.py
After a few seconds to load, you should see the RouterSploit splash screen. From here, the interface is similar to Metasploit, with the primary commands being:
use (module)
set (variable)
show options (shows module options)
check (checks to see if target is vulnerable to exploit)
run (runs the exploit module against the target)
The module we'll be running is Autopwn, which we can select by typing the following.
use scanners/autopwn
This will open the Autopwn scanner to begin scanning a target.
Step 5Setting & Prosecuting a Target
With the Wigle Wifi Wardriving app installed on your Android phone, it's easy to see nearby wireless networks. As soon as you gain access to a Wi-Fi network, either an open network or by gaining the password, you'll be able to scan the network to find all devices on it with Fing or another network scanner.
Once you locate the IP address of your target, it's time to put it into Autopwn. To see the available options on any module, type the following.
show options
In this case, we'll be setting the target IP to that of the router we want to attack. To do so, enter this into the terminal:
set target IP_address_here
 Here, we set the target for the Autopwn scan with the IP address of the target.
Here, we set the target for the Autopwn scan with the IP address of the target.Replace IP_address_here with the IP address of the router, and hit enter. This should set the target to the router. To double check, type show options again. When you're satisfied with the result, type run and hit enter to begin the module. The module will run, presenting a list of found vulnerabilities at the end of the scan.

Here, we see a scanning run starting against a target.
Step 6Exploiting Found Vulnerabilities
When Autopwn finds a vulnerability, exploiting it couldn't be easier. After the scan is complete, type use and then copy and paste the path provided by Autopwn to the exploit. For example, running the exploits/cameras/dlink/dcs_9301_9321_auth_bypasswould be done by typing:
use exploits/cameras/dlink/dcs_9301_9321_auth_bypass
As before, we can set the target with:
set target IP_address_here
Once the target is set to our desired IP address, you can run check to verify the device is vulnerable. When you're ready to exploit, type run and the exploit module will run.

This device is vulnerable!
Warning
Even if the router is left completely undefended and is easy to pwn, that doesn't make it legal. Make sure you have permission to audit the router you're pwning, as the Autopwn scanner makes a lot of noise and may be detected by active security measures.
No comments:
Post a Comment